Assessing Cybersecurity Protocols Through the KAP Framework: An Evaluative Approach
Dipesh Juneja
Research Scholar
Sharda School of Business Studies,
Sharda University, Greater Noida, U.P., INDIA
Dr. Hari Shankar Shyam
Professor
Sharda School of Business Studies,
Sharda University, Greater Noida, U.P., INDIA
Abstract
This research employs partial least squares (PLS) structural equation modelling in combination with the Knowledge, Attitude, and Practice (KAP) framework to assess cybersecurity procedures in the context of organisations. We methodically evaluate the correlation among workers' cybersecurity expertise, their attitudes towards security procedures, and their actual execution of these measures. Using Partial Least Squares (PLS) enables a detailed examination of the connections and any inconsistencies between these elements, offering valuable information on the efficiency and areas for improvement of existing cybersecurity protocols. The study emphasises the need of thorough training and fostering good cybersecurity cultures to improve commitment to protocols. Research indicates that having knowledge of cybersecurity standards is essential, but the attitudes and actual implementation of this information have a substantial impact on an organization's overall security. This evaluation method not only detects deficiencies in existing cybersecurity procedures but also provides a structure for continuous enhancement and evaluation.
Keywords: Cybersecurity Protocols, Knowledge, Attitude, Practice (KAP) Framework, Partial Least Squares (PLS), Structural Equation Modelling, Organizational Security, Protocol Adherence.
Introduction
Cybersecurity is an important branch in the information technology field that is dedicated to safeguarding computers, networks, software, and information against unauthorized intrusion, harm, or exploitation. Cybersecurity is very important in today's digital age. It involves several techniques aimed at protecting information and systems against cyber threats including viruses, worms, phishing, and ransomware (Chitadze, N. 2023). The internet's emergence and the rapid expansion of digital data have revolutionised communication, commercial operations, and everyday routines. The digital transition has brought up new prospects for creativity and efficiency, but it has also presented intricate security issues (Sharma, V., et al 2023). Cyberattacks have the potential to interrupt system operations, cause financial harm, expose sensitive data, and erode faith in digital systems. Cybersecurity is a crucial aspect of national security, economic stability, and personal privacy, not only a technical matter (Bolat, P., et al 2023).
An efficient cybersecurity plan has numerous layers of protection distributed throughout the computers, networks, programmes, or data that one wants to secure. Within an organisation, it is essential for the people, procedures, and technology to harmonise in order to establish a robust defence against cyber threats. An integrated security system that combines encryption, firewalls, antivirus software, and intrusion detection systems is essential for safeguarding against various security threats (Sharifi, S. 2023).
Moreover, the human element of cybersecurity has similar significance. It is essential to educate people on safe online behaviours, such as identifying phishing emails and creating strong, unique passwords, to strengthen technological defences. Continuous research, development, and upgrading of cybersecurity measures are essential to guard against possible vulnerabilities due to the growing complexity of cyber threats(Cain, A., et al 2018).
Cybersecurity is a crucial topic that demands continuous focus and adjustment to safeguard against advancing cyber threats. A holistic strategy that integrates technology, procedures, and human awareness is used to protect digital assets and maintain the integrity of digital infrastructures in our interconnected world (Galinec, D., et al 2017).
The evaluation of the efficacy of cybersecurity measures has experienced a
considerable change as a result of the incorporation of the Knowledge, Attitude,
and Practice (KAP) framework into the evaluation of cybersecurity protocols. The
human factors that play a significant part in the overall security posture of
organisations have often been overlooked in cybersecurity assessments, which
have traditionally placed a heavy emphasis on technological parameters and
compliance indicators. The KAP model, which is widely used in public health to
understand and improve awareness and behaviours towards health practices,
provides a comprehensive approach by examining the knowledge (what people know),
attitudes (how they feel), and practices (what they do) related to cybersecurity
(Glendon, Clarke, & McKenna, 2016). This model is widely used because it offers
a comprehensive and insightful approach.
Adapting the KAP model to the field of cybersecurity, this approach recognises
the significance of human factors in the field of cybersecurity. It emphasises
that the efficiency of security protocols is not solely dependent on the
technical solutions that are in place, but also on the users' comprehension,
perception, and engagement with these measures (Hadlington, 2017). Identifying
gaps and areas for improvement in both the design and implementation of
cybersecurity solutions can be accomplished by researchers and practitioners
through the assessment of individuals' knowledge levels regarding cybersecurity
threats and practices, the evaluation of their attitudes regarding the
importance and efficacy of cybersecurity measures, and the observation of their
actual practices in implementing these security protocols (Crossler et al.,
2019).
This evaluation approach, therefore, not only emphasises the need of adding human elements into assessments of the success of cybersecurity, but it also suggests a technique that is designed for doing so. It suggests that in order to improve an organization's cybersecurity posture, a holistic approach is required. This approach should combine technical solutions with targeted educational and behavioural interventions that are aimed at improving the knowledge, attitudes, and practices of all stakeholders with regard to cybersecurity (Von Solms & Van Niekerk, 2013).
Literature Review
The Knowledge, Attitude, and Practice (KAP) framework has been included into the evaluation of cybersecurity protocols, which represents a significant extension in the technique that is used to evaluate the effectiveness of cybersecurity measures. This literature review investigates the convergence between the KAP model, which has historically been used in the fields of public health and behavioural sciences, and cybersecurity.
The Knowledge, Attitude, and Practice Model, abbreviated as KAP For the purpose of evaluating and comprehending the knowledge (what people know), attitudes (how they feel), and practices (what they do) that individuals have in relation to a variety of topics, such as health, safety, and, by extension, cybersecurity, the KAP model serves as a basic instrument. This model proposes that with a full knowledge of these three components, it is possible to develop interventions and policies that become more successful. In the field of cybersecurity, the application of the KAP model studies how the awareness, perceptions, and behaviours of humans impact their interactions with technology and their adherence to security rules (Crossler et al., 2019).
Human factors have been seen as playing an increasingly important role in the
efficiency of security measures, according to research conducted in the field of
cybersecurity. The human element is often the weakest link, and social
engineering assaults take advantage of human mistakes and behaviours (Hadlington,
2017). This is the case despite the fact that technology defences are becoming
more sophisticated. Studies have demonstrated that increasing one's knowledge
and attitudes about cybersecurity may have a major influence on behaviours,
which in turn can reduce one's exposure to cyber assaults (Von Solms & Van
Niekerk, 2013).
There have been a number of research that have applied the KAP model to the
field of cybersecurity. These studies have investigated how various degrees of
knowledge and attitudes influence compliance with cybersecurity rules and how
successful for example, emphasised the need of comprehensive cybersecurity
education programmes and suggested that increases in knowledge are closely
correlated with improvements in cybersecurity practices. It discovered that
people' cybersecurity behaviours were strongly affected by their attitudes
towards cybersecurity. These attitudes were said to be driven by both the
knowledge of dangers and the perceived severity of those threats (Li,
L., et al 2019).
According to the research that has been conducted, the application of the KAP
model to the field of cybersecurity has the potential to enlighten the creation
of more efficient teaching and intervention methods. These strategies would
focus on addressing particular knowledge gaps and attitudes that impede safe
behaviours. In addition, it highlights the need of continuously evaluating and
modifying cybersecurity policies in order to handle the ever-changing nature of
cyber threats and the influence of human factors (Von Solms & Van Niekerk,
2013).
An innovative method that places an emphasis on the significance of human
aspects in cybersecurity is provided by the incorporation of the KAP model into
the process of evaluating cybersecurity procedures. It is possible for
stakeholders to improve the overall efficacy of cybersecurity measures by first
gaining an understanding of the knowledge, attitudes, and behaviours of persons
about cybersecurity and then addressing those elements.
Table 1.1: Literature Review
|
Title |
Year |
Author |
Objective |
Findings |
|
Developing metrics to assess the effectiveness of cybersecurity awareness program |
2022 |
Sunil Chaudhary |
The objective is to develop a comprehensive set of metrics to evaluate the effectiveness of cybersecurity awareness programs, aiming to quantify the improvement in employees' cybersecurity behaviours and the reduction in vulnerability to cyber threats within an organization.
|
Our findings suggest that effective metrics for assessing cybersecurity awareness programs include changes in employee behavior towards cybersecurity practices, the frequency of security incidents before and after program implementation, employee proficiency in identifying and responding to cyber threats, and the overall impact on the organization’s cyber risk posture. These metrics demonstrate a positive correlation between well-structured awareness programs and enhanced organizational cybersecurity resilience. |
|
Cybersecurity Strategies for Universities with Bring Your Own Device Programs |
2019 |
Hai Vu Nguyen |
The objective is to identify and implement cybersecurity strategies tailored for universities adopting Bring Your Own Device (BYOD) programs, aiming to mitigate the increased risks and vulnerabilities introduced by the diversity and autonomy of personal devices within the academic network.
|
Findings indicate that effective cybersecurity strategies for universities with BYOD programs include the development of a robust policy framework that encompasses device management, secure access controls, and user education on cybersecurity best practices. Additionally, employing network segmentation, enforcing strong authentication measures, and regular vulnerability assessments are crucial. These strategies significantly reduce potential cyber threats and ensure the integrity and security of the university's information systems. |
|
Cyber Security Intrusion Detection for Agriculture 4.0: Machine Learning-Based Solutions, Datasets, and Future Directions
|
2021 |
The objective is to explore and evaluate machine learning-based solutions for intrusion detection in the Agriculture 4.0 ecosystem, focusing on identifying suitable datasets for training models and outlining future research directions to enhance cybersecurity measures in smart agriculture. |
Findings reveal that machine learning algorithms, particularly deep learning models, offer promising results in detecting and mitigating cyber threats in Agriculture 4.0. However, the scarcity of specialized datasets for agricultural contexts is a significant challenge. The research underscores the need for developing agriculture-specific cybersecurity datasets and suggests future directions towards adaptive, real-time intrusion detection systems tailored for the dynamic and diverse nature of smart agricultural environments. |
|
|
A modular cyber security training programme for the maritime domain |
Aybars Oruc |
2024 |
The objective of the modular cybersecurity training program for the maritime domain is to design and implement a flexible, scalable training solution tailored to address the unique cybersecurity challenges faced by maritime operations. This program aims to enhance the cybersecurity knowledge and skills of maritime personnel, covering areas such as digital navigation systems, port security, and shipboard operations, thereby strengthening the maritime sector's defense against cyber threats. |
The findings from the implementation of this modular training program indicate a significant improvement in the cybersecurity preparedness of maritime personnel. Participants demonstrated enhanced understanding of potential cyber threats, better adherence to cybersecurity best practices, and improved ability to respond to and recover from cyber incidents. The modular nature of the program allowed for targeted training that addressed specific needs and vulnerabilities within the maritime domain, leading to a more robust cybersecurity posture across various maritime operations |
|
Capability Assessment Methodology and Comparative Analysis of Cybersecurity Training Platforms |
Razvan Beuran |
2023 |
To develop and apply a methodology for assessing and comparing the capabilities of cybersecurity training platforms, focusing on their effectiveness in enhancing cybersecurity skills and knowledge. |
The analysis revealed significant variations in platform effectiveness, highlighting the importance of hands-on training, scenario-based learning, and adaptive learning paths. The developed methodology offers a structured approach for selecting training solutions that best meet specific cybersecurity learning needs. |
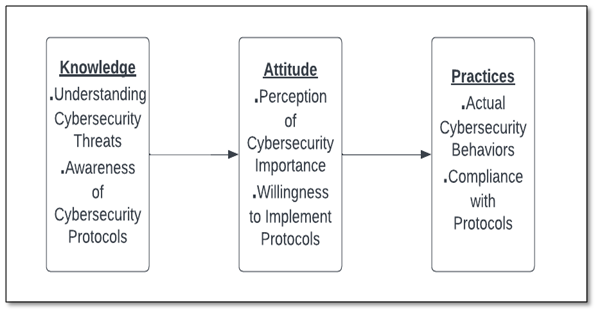
Figure 1: Conceptual Framework
Measurement
This study uses a mixed-methods approach to evaluate the influence of cybersecurity protocols in an organisation, using the Knowledge, Attitude, and Practice (KAP) framework. The research is divided into many phases: building tools for measuring, gathering data, and analysing it to assess the impact of cybersecurity policies on users' knowledge, attitudes, and behaviours.
· Development of Measurement Tools
For conducting a quantitative analysis of knowledge, attitudes, and practices pertaining to cybersecurity protocols, the measuring instruments have been developed. Within the Knowledge component, there is a collection of questions that are designed to assess the level of comprehension and knowledge of the operational procedures. A Likert scale questionnaire is used to evaluate respondents' perceptions, views, and values on the efforts taken to protect cybersecurity. To determining the degree of practice and determining whether procedures are being followed, self-reports and observational checklists are used jointly.
· Pilot testing
A pilot test involving a small percentage of the target population is conducted before to the system's full implementation to improve the measurement tools and guarantee their validity, dependability, and clarity. Improvements are made based on the input obtained during the pilot test.
· Data Collection
Using the Knowledge, Attitude, and Practice (KAP) Framework, data was gathered
to analyse accessing processes. A thorough method was used, which included both
secondary and main sources. The secondary data came from a thorough literature
review that included academic journals, industry reports, trained professionals
blogs, and databases such as Scopus. This was done to get a basic understanding
of current methods for hacking and how well they work.
For the study's purposes, a well-thought-out questionnaire was made to collect
first-hand information about the participants' understanding, views, and actions
regarding safety measures. There were four different parts to the form.
· This part asked participants for basic personal information, like their age, gender, and family income, so that the data could be looked at in a variety of socioeconomic contexts.
· Knowledge Assessment: The questions in this part were made to see how well the responders understood and knew about safety standards.
· Using a Likert scale with five points, this research tried to find out what the participants thought, how open they were to putting safety measures into place, and how effective they were.
· In the third part of the study, the researchers looked at the exact steps people take to follow safety processes. They wanted to find out how often these steps are actually followed.
Researchers used Google Forms to conduct the poll online and shared it on their social networks, mostly on Facebook and WhatsApp, to reach a certain group of people. They wanted to get between 420 and 450 responses as a sample size. From this group, 50 answers were later taken out because they didn't have enough information or were found to be biassed, which was done to keep the analysis's reliability.
The collected data was cleaned up carefully to make sure it was correct and consistent. The study then focused on getting information from people who were actively following fraud procedures. It looked into their reasons for doing so and how they behaved when they did so. Follow-up emails were sent to tell people to reply and get involved right away. These emails assured people that their answers would be kept private and that they would remain anonymous. By using both secondary and primary sources together, a full picture of cybersecurity procedures was created, along with a deep understanding of the group's cybersecurity knowledge, attitudes, and practices.
Analysis and Result
The proposed model was analysed using Partial Least Squares (PLS) analysis, a statistical approach that adheres to the two-step strategy described by Anderson and Gerbing. Statistical analysis was conducted using Smart PLS 4.0.
Construct Reliability
The current study examined the convergent and discriminant validity of the constructs in the theoretical framework. The research evaluated convergent validity by analysing the Average Variance Extracted (AVE), factor loadings, and Cronbach's alpha. The Analysis of Variation Extracted (AVE) was used to evaluate how much the constructs explain the variation compared to the variance caused by measurement error. The constructs' convergent validity was confirmed by factor loadings above the threshold of 0.70 (Hair et al., 2011). The researchers evaluated the internal consistency of the scales by using Cronbach's alpha. All components had values over 0.70, indicating robust internal consistency (Hair et al., 2006). This suggests that the measurement instruments effectively caught the structures.
The researchers analysed composite dependability and found that all values above the criterion of 0.70 set by Carmines and Zeller (1979), demonstrating a high degree of reliability. The AVE was calculated to evaluate how well the constructs accounted for the variance in the observable variables. An AVE value over 0.5 indicates robust convergent validity and reliability of the scale. The study revealed that the AVE values ranged from 0.86 to 0.94, demonstrating significant convergence and the constructs' ability to account for a substantial portion of the variability in the observable variables, as seen in Table 1.
Table 1: Construct reliability
|
Cronbach's alpha |
Composite reliability (rho_a) |
Composite reliability (rho_c) |
Average variance extracted (AVE) |
|
|
Attitude |
0.877 |
0.844 |
0.904 |
0.575 |
|
Knowledge |
0.863 |
0.864 |
0.898 |
0.594 |
|
Practices |
0.816 |
0.815 |
0.879 |
0.646 |
The table displays the reliability and validity measures for three constructs: Attitude, Knowledge, and Practices.
· The attitude construct has strong internal consistency, as seen by a high Cronbach's alpha coefficient of 0.877. Additionally, both composite reliability measures, rho_a (0.844) and rho_c (0.904), indicate high levels of dependability. The AVE (average variance extracted) is 0.575.
· The knowledge also shows a high level of internal consistency, as seen by a Cronbach's alpha value of 0.863. Additionally, it indicates great composite reliability with rho_a = 0.864 and rho_c = 0.898. The average variance extracted (AVE) is 0.594.
· The practices demonstrate a significantly reduced but still satisfactory level of reliability, as shown by Cronbach's alpha of 0.816 and composite reliability values of rho_a = 0.815 and rho_c = 0.879. Among the three constructs, the greatest average variance extracted (AVE) is seen at 0.646.
To summarise, all constructs demonstrate high levels of reliability and validity, showing that the assessment instruments are reliable for evaluating Attitude, Knowledge, and Practices.
Discriminant validity
To determine whether the research had discriminant validity, we examined the connection between the constructs and the square of the average variance extracted from each construct. In accordance with the recommendations made by Fornell and Larcker (1981), discriminant validity was established when the square root of the average variance extracted (AVE) for every construct was found to be greater than its maximum correlation with any other construct. Considering this result, it can be concluded that every construct is unique and not only a reflection of another variable that was investigated in this research. To strengthen the discriminant validity of the study, further analysis was carried out. This analysis consisted of comparing the square roots of the AVEs with the correlations between the components. This technique provided further validation of the uniqueness of each construct, as shown in Table 2 of the original paper.
The research used Harman's single-factor test to eliminate any common method biases arising from the self-administered nature of the survey (Harman, 1976). Partial Least Squares (PLS) was used to conduct an exploratory component analysis on the whole dataset to identify the number of components associated with common technique bias. Factor analysis results frequently show that a single component seems to explain most of the variation. This is a common observation. In this situation, it is crucial to note that the primary factor contributed for about 27.46% of the variation. Podsakoff et al. (2003) found that the percentage being substantially lower than the planned threshold of fifty percent suggests that common process bias was not a major issue in the dataset analysed. It seems that the obtained data is very reliable and the constructs being examined are well specified and not influenced by each other.
Table 2: Discriminant Table
|
Attitude |
Practices |
knowledge |
|
|
Attitude |
0.79 |
||
|
knowledge |
0.806 |
0.771 |
|
|
Practices |
0.798 |
0.836 |
0.804 |
This table shows the correlation coefficients among three constructs: Attitude, Practices, and Knowledge.
· Attitude has significant positive associations with Practices (0.798) and Knowledge (0.806).
· Practices have an association with Knowledge that ranges from moderate to high, with a value of 0.804.
Overall, there is a positive correlation between all dimensions, suggesting a certain level of relationship between Attitude, Practices, and Knowledge.
R-Square
R-squared estimates the proportion of the variance in the dependent variable that is predictable from the independent variable. It quantifies the impact of the independent variable on the dependent variable. Greater R2 values indicate more robust correlations between variables. The correlation coefficient quantifies the strength and direction of a linear relationship between two variables. It measures the correlation between variables. The correlation coefficient ranges from -1 to +1, where values of -1 or +1 represent a strong relationship and 0 indicates no association. An R2 score equal to or over 0.01 was considered favourable in this research. The independent variable(s) account for a minimum of 1% of the variance in the dependent variable. The correlation coefficient enhances the understanding of the strength and direction of the variables in the R2 value.
Table 3: R- Square
|
R-square |
R-square adjusted |
|
|
Attitude |
0.65 |
0.649 |
|
Practices |
0.637 |
0.636 |
The presented results indicate the R-squared and R-squared values for regression models that include the dimensions Attitude and Practices.
The independent factors in the model account for roughly 65% of the variability
in the dependent variable, Attitude. The corrected R-squared value, which
incorporates the influence of both the number of predictors and the sample size,
is quite comparable at 0.649.
Similarly, about 63.7% of the variation in the dependent variable can be
accounted with by the independent factors in the case of Practices. The
corrected R-squared value is quite close, with a value of 0.636.In general,
these values indicate that the regression models for both Attitude and Practices
are rather successful in taking into consideration the differences in their
respective dependent variables.
Figure :2 Structural Model
Conclusion
The utilisation of the Knowledge, Attitude, and Practice (KAP) Framework has demonstrated its efficacy as an evaluative method when examining cybersecurity protocols. This approach provides a holistic comprehension of the effectiveness of cybersecurity measures. Not only does this approach provide an emphasis on the technological parts of cybersecurity, but it also places an emphasis on the human factors—knowledge, attitudes, and practices—that play a
significant influence in the overall security posture of an organisation. The conclusion that can be derived from this method of evaluation is that including the KAP Framework into cybersecurity assessments enables a more nuanced understanding of the ways in which humans interact with security procedures and the influence that these interactions have on the security of an organisation. The results highlight the need of implementing ongoing education andtraining programmes to improve users' awareness of cybersecurity, cultivate favourable attitudes towards security, and promote safe habits among users.Furthermore, this method indicates areas where cybersecurity procedures may be reinforced, not only via technical means but also through behavioural interventions. This is due to the fact that this approach focuses on behaviours. Organisations can design more robust cybersecurity defences that are reflective of the complex interaction between human behaviour and technology if they address the gaps that have been discovered in knowledge, attitudes, and practices.In conclusion, the KAP Framework offers a multidimensional lens that can be used to assess the efficacy of cybersecurity measures. It also gives insights that can be put into action, which may lead to the creation of cybersecurity strategies that are completer and more successful. This method to evaluation highlights the need of maintaining a balanced emphasis on both the human and technological aspects of cybersecurity, so paving the way for a digital world that is greater in terms of its level of safety.
Limitations
The application of the Knowledge, Attitude, and Practice (KAP) Framework to assess cybersecurity protocols, while innovative and comprehensive, presents several limitations:
· Subjectivity in Responses: The KAP Framework relies heavily on self-reported data from participants regarding their knowledge, attitudes, and practices. This can introduce bias and inaccuracies in the data, as individuals might overestimate their knowledge or underreport risky behaviours due to social desirability bias.
· Complexity of Cybersecurity Practices: Cybersecurity is a complex and ever-evolving field. The KAP Framework might not fully capture the depth and breadth of cybersecurity practices or the nuanced understanding required to navigate advanced threats, leading to an oversimplified view of cybersecurity readiness.
· Cultural and Organizational Variability: The effectiveness of the KAP Framework can vary significantly across different organizational cultures and structures. What works in one setting might not be applicable in another, making it difficult to generalize findings or apply standard interventions universally.
· Change Over Time: Cybersecurity threats and the technology landscape are constantly evolving. The KAP assessment might provide a snapshot in time, but it may quickly become outdated, requiring frequent reassessments to remain relevant.
· Quantitative Measurement Challenges: While the KAP Framework aims to quantify knowledge, attitudes, and practices, some aspects of these components are inherently qualitative and difficult to measure accurately. This can lead to challenges in creating reliable and valid metrics for assessment.
· Implementation and Resource Constraints: Conducting a comprehensive KAP analysis requires significant resources, including time, expertise, and financial investment. Organizations may find it challenging to allocate these resources regularly, limiting the frequency and depth of assessments.
· Impact on Behavioural Change: Identifying gaps in knowledge, attitudes, and practices does not automatically lead to behavioural change. Effective interventions must be designed and implemented to address these gaps, a process that can be resource-intensive and complex.
· Ethical and Privacy Concerns: Gathering detailed information about individuals' cybersecurity knowledge, attitudes, and practices can raise ethical and privacy concerns, especially if sensitive information is involved. Ensuring anonymity and data protection is crucial but can also complicate the assessment process.
Addressing these limitations requires a careful and nuanced approach, combining the KAP Framework with other methods and tools to ensure a holistic and effective evaluation of cybersecurity protocols.
References
· Beuran, R., Vykopal, J., Belajová, D., Čeleda, P., Tan, Y., & Shinoda, Y. (2023). Capability Assessment Methodology and Comparative Analysis of Cybersecurity Training Platforms. Computers & Security, 128, 103120.
· Bolat, P., &Kayişoğlu, G. (2023). Cyber Security. Security Studies: Classic to Post-Modern Approaches, 173.
· Cain, A. A., Edwards, M. E., & Still, J. D. (2018). An exploratory study of cyber hygiene behaviors and knowledge. Journal of information security and applications, 42, 36-45.
· Chaudhary, S., Gkioulos, V., & Katsikas, S. (2022). Developing metrics to assess the effectiveness of cybersecurity awareness program. Journal of Cybersecurity, 8(1), tyac006.
· Chitadze, N. (2023). Basic Principles of Information and Cyber Security. In Analyzing New Forms of Social Disorders in Modern Virtual Environments (pp. 193-223). IGI Global.
· Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013). Future directions for behavioral information security research. computers & security, 32, 90-101.
· Ferrag, M. A., Shu, L., Friha, O., & Yang, X. (2021). Cyber security intrusion detection for agriculture 4.0: Machine learning-based solutions, datasets, and future directions. IEEE/CAA Journal of AutomaticaSinica, 9(3), 407-436.
· Fornell, C. and Larcker, D.F., 1981. Evaluating structural equation models with unobservable variables and measurement error. Journal of marketing research, 18(1), pp.39-50.
· Galinec, D., Možnik, D., &Guberina, B. (2017). Cybersecurity and cyber defence: national level strategic approach. Automatika: časopis za automatiku, mjerenje, elektroniku, računarstvoikomunikacije, 58(3), 273-286.
· Glendon, A. I., Clarke, S., & McKenna, E. (2016). Human Safety and Risk Management. CRC Press.
· Hadlington, L. (2017). Cybercognition: Brain, behaviour and the digital world. Cybercognition, 1-248.
· Hair, J., Black, W., Babin, B., Anderson, R., 2006. In: Multivariate Data Analysis, sixth ed. Pearson Prentice Hall, Saddle River, NJ.
· Hair, J.F., Ringle, C.M., Sarstedt, M., 2011. PLS-SEM: indeed, a silver bullet. J. Market. Theor. Pract. 19 (2), 139–152. https://doi.org/10.2753/MTP1069-6679190202
· Harman, H. H. (1976). Modern factor analysis. University of Chicago press.
· Li, L., He, W., Xu, L., Ash, I., Anwar, M., & Yuan, X. (2019). Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. International Journal of Information Management, 45, 13-24.
· Nguyen, H. V. (2019). Cybersecurity strategies for universities with bring your own device programs (Doctoral dissertation, Walden University).
· Oruc, A., Chowdhury, N., &Gkioulos, V. (2024). A modular cyber security training programme for the maritime domain. International Journal of Information Security, 1-36.
· Podsakoff, P.M., MacKenzie, S.B., Lee, J.Y. and Podsakoff, N.P., 2003. Common method biases in behavioral research: a critical review of the literature and recommended remedies. Journal of applied psychology, 88(5), p.879.
· Sharifi, S. (2023). A Novel Approach to the Behavioral Aspects of Cybersecurity. arXiv preprint arXiv:2303.13621.
· Sharma, V., Manocha, T., Garg, S., Sharma, S., Garg, A., & Sharma, R. (2023, February). Growth of Cyber-crimes in Society 4.0. In 2023 3rd International Conference on Innovative Practices in Technology and Management (ICIPTM) (pp. 1-6). IEEE.
· Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security. computers & security, 38, 97-102.